views

Mobile apps are part of our daily lives. From checking the news and ordering food to banking and chatting with friends, apps are everywhere. But with this convenience comes a risk: mobile apps can be a target for hackers and cybercriminals.
That’s where a Mobile Application Security Expert comes in. Their job is to make sure your app is safe from all sorts of threats, protecting both your data and your users. But how do they do that? We’ll take a deep dive into the role and how they keep your app secure.
What Does a Mobile Security Expert Do?
A person with expertise in locating, resolving, and averting security flaws in mobile applications is known as a mobile security expert. To create robust defenses against potential threats, they collaborate closely with developers, product managers, and cybersecurity teams.
Their main goal is to protect apps from:
-
Data theft
-
Malware infections
-
Unauthorized access
-
Insecure communication
-
Fraudulent activities
Consider them to be your mobile app's virtual bodyguard.
Why Mobile App Security Is Important
Imagine discovering that your personal information has been compromised after downloading a banking app. or utilizing a messaging service that allows third parties to see your private messages. It's frightening, isn't it?
Risks like these are extremely real. Sensitive information, including passwords, bank account information, and private messages, is frequently stored in mobile apps. This data could end up in the wrong hands if the software isn't secure.
A security breach can:
-
Damage your brand reputation
-
Lead to financial losses
-
Cause legal issues
-
Break the trust of your users
To prevent these issues before they arise, businesses use experts.
Step-by-Step: How a Mobile Security Expert Protects Your App
Let's review the key steps that a mobile security expert takes to protect your app.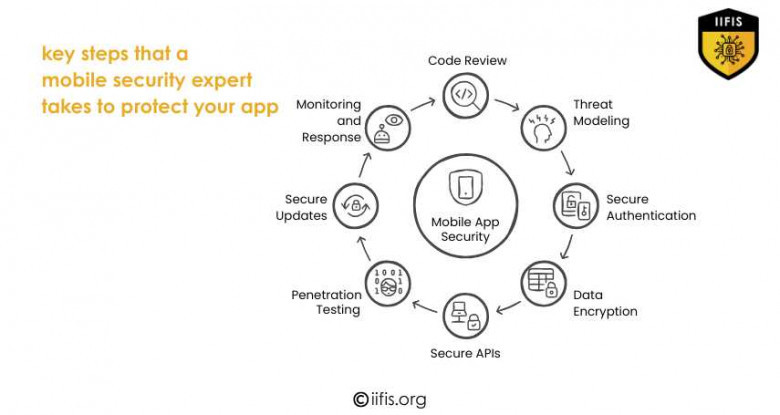
1. Code Review and Static Analysis
Reviewing the app's source code is frequently the first step taken by a security expert. They search for out-of-date libraries, risky coding techniques, and hardcoded sensitive information (such as keys or passwords).
They may use tools like:
-
Static Code Analyzers: These tools scan code for known vulnerabilities.
-
Manual Code Reviews: To identify minor problems, experts closely examine important sections of the code.
2. Threat Modeling
The security expert tries to think like the hackers before they can get into an app. We refer to this as threat modeling. They examine the app's data flow and pinpoint potential attack points.
They ask questions like:
-
Where is the data stored?
-
How is it transferred?
-
Who can access it?
-
What happens if someone tampers with it?
This helps in their early defensive strategy planning.
3. Secure Authentication and Authorization
The goal of authentication is to confirm a user's identity. Verifying their permission is the goal of authorization. Both are essential.
Experts ensure that:
-
Passwords are safely kept.
-
Authentication using multiple factors is activated.
-
Sessions are appropriately run.
-
Access restrictions are stringent and clearly stated.
By taking these precautions, you can be sure that only authorized users can use the software.
4. Data Encryption
Encryption is similar to creating a hidden code out of your data. They won't be able to read it even if they steal it.
Security experts use encryption:
-
While the device is at rest and saving data.
-
While data is being transmitted (in transit) between the application and the server.
To protect privacy, they use robust encryption protocols like TLS and AES.
5. Secure APIs and Backend
In order to retrieve or transmit data, mobile apps frequently communicate with a server. We refer to these as APIs. Attackers can alter and steal data from APIs that are not secure.
An expert:
-
Verifies all data coming in and going out.
-
Uses tokens and API keys to restrict access.
-
Stops typical threats, including cross-site scripting (XSS) and SQL injection.
Weak server connectivity is the source of many app vulnerabilities, so this step is essential.
6. Regular Penetration Testing
Pen testing, also known as penetration testing, is similar to employing ethical hackers to attempt to compromise your application. Experts in mobile security conduct this to identify the app's vulnerabilities.
They test how well the app defends itself by simulating actual attacks. After that, they address the problems before real hackers can take advantage of them.
7. Secure Updates and Patching
New dangers may surface even after an app has been deployed. For this reason, it's critical to maintain the app's updates.
Security experts:
-
Keep an eye out for fresh vulnerabilities in SDKs and libraries.
-
Release security updates on time.
-
Make sure the app isn't broken by testing every update.
Updates are an essential component of software security and go beyond simply adding new features.
8. Monitoring and Incident Response
Things can still go wrong even with all the precautions. For this reason, mobile security professionals install monitoring systems to find questionable activity.
They start an investigation right away if something odd occurs, such as an abrupt increase in login attempts.
Additionally, they are prepared with an incident response strategy. This comprises:
-
Isolating the threat
-
Fixing the vulnerability
-
Notifying affected users
-
Reporting to regulatory bodies (if required)
Common Threats That Mobile Security Experts Defend Against
Security professionals aggressively defend applications against the following frequent threats:
-
Man-in-the-middle attacks: These occur when hackers eavesdrop on conversations between the server and the application.
-
Reverse engineering: The process by which someone looks for secrets in an application by reading and comprehending its code.
-
Rooting or jailbreaking: When consumers take away security features from their devices, apps become vulnerable.
-
Malicious apps: Phishing apps that aim to deceive users and steal data.
-
Insecure storage: Placing private information in plain text for easy access.
Experts create more effective defenses by understanding these hazards.
How to Know If Your App Needs a Mobile Security Expert
Every app needs some level of security. But if your app does any of the following, an expert is a must:
-
Handles user accounts or logins.
-
Stores or transfers sensitive data.
-
Includes in-app purchases or payments.
-
Accesses phone features like camera, location, or contacts.
-
Connects to external APIs or cloud services.
In other words, if your app does more than just display static content, you need an expert on your team.
Mobile applications are effective tools, but they also carry a lot of responsibility. When users launch your app, they trust you with their data. It is necessary to acquire and uphold such trust.
In order to maintain confidence, a Mobile Security Expert is your partner. They are essential to the success of your app since they secure data and stop hacks.
It makes sense to work with a qualified mobile security specialist if you're serious about creating a secure app. Search for experts with recognized qualifications such as the IIFIS Certified Mobile Application Security Expert. They will be trained in the most recent methods and standards because of this.










